Title: Cybercrimes in the Eswatini banking sector: Implementing Routine Activity Theory analysis
Mr Emmanuel Lungile Howe, First Author: lungile.howe@gmail.com
iD orcid.org/0000-0002-3142-9585
Senior lecturer, Faculty of Computing at Botho University Eswatini, PhD student, NWU, Mahikeng campus —Business School.
MTech in Information Systems (Tshwane University of Technology (TUT)), Bachelor’s Degree in Information Technology.
Co-author: Professor Anna-Marie (AMF) Pelser – anna.pelser@hotmail.com
iD orcid.org/0000-0001-8401-3893
Research Professor, North-West University, Faculty of Economic and Financial Sciences — Entity Director —GIFT, Mafikeng Campus.
HED (Home Economics, PU for CHE), B Com (UNISA), B Com Hons (PU for CHE), M Com (Industrial Psychology, NWU), PhD (Education Management, NWU).
Corresponding author Prof A.M.F. Pelser – ampelser@hotmail.com
Ensovoort, volume 43 (2022), number 7: 5
Abstract
Cybercrime is now viewed as one of the top 10 global risks in organisations especially for developing countries. The heavy dependency on electronic and digital tools to carry out business and financial transactions indicates that a serious threat has also been imposed as to the safety and reliability of financial operations. Although banks continue to invest in controls and measures to fight cybercrime, the threat still remains. The continuous migration and adoption of technology in cyberspace also contributes towards the opportunity for cybercrime to happen. This study explores the context of cybercrime in banks through reports from organisations and industry experts. The study involved three banking institutions and the aim was to investigate the prevalence of cybercrime in Eswatini banks. The study revealed ATM fraud, card cloning, investment fraud and Internet fraud as the most common type of cybercrime affecting Eswatini banks. The findings show that although banks have systems in place to curb cybercrime; however the pace in which cybercriminals continuously find new ways to evade such systems, increases at an alarming rate. From the industry-expert perspective, there was a good foundation regarding the knowledge of cybercrime and related attacks.
Keywords: Cybercrime, Routine Activity Theory, banking sector
1. Introduction
The banking industry has become one of the most important institutions for any country and has become central to the lives of citizens. The digital space particularly the Internet has played a role towards the growth of this industry. However this growth has exposed the industry to cybercrime. The banking sector remains a top-targeted industry in Africa especially for cybercriminal activities and as a result the cyberattacks have become more targeted, complicated and difficult to prevent (Emm, 2020).
The expansion and rapid adoption of ICTs and Internet penetration has also raised concerns about cybercrime (Symantec, 2018). Gradually, cybercriminals have taken advantage by using their skills to steal information from unsuspecting customers or individuals and they have become skilled at understanding psychology and in most situations use social engineering tactics to exploit human vulnerability (Chigada, 2020). The South African Banking Risk information Centre (SABRIC) states that South Africa loses approximately $157 million annually to cyberattacks (Kshetri, 2019:1). In the Kingdom of Eswatini, the Central Bank of Eswatini fell victim to cybercrimes of data breach and fraud in 2013 and 2016, and it resulted in a loss amounting to E7.5 million, although the fraud attempt totalled E21 million (Thwala, 2019:15). Financial losses by the banking industry worldwide as a result of white collar crimes are in huge amounts and far outweigh conventional methods of bank robbery (Bamrara, Singh & Bhatt, 2013).
The role of the Internet has enabled the transformation of cybercrime activities in generational stages. The first generation of cybercrime occurred within discrete computing systems and was characterized by exploitation activities. It paved the way for departure from the conventional criminal activity. The second generation of cybercrime occurred across networks, and involved acts such as hacking and cracking. The third generation is characterized by its dispersed and automated nature entailing computer systems interaction (Wall, 2007:44-47).
Cybercrime is a form of crime that includes traditional crime such as fraud, identify theft and child pornography, which is performed through the unauthorized access, damage and interference with a computer system, (Broadhurst, 2006). Cybercrime is a severe threat to all sectors of the economy of a country and the banking sector has not been spared. The rise of cybercrime globally has caused a series of problems amounting to millions of dollars and has resulted in cybercrime being viewed as a lucrative business where the cybercriminals target their victims anonymously using malicious online software that hides their online activities (Vineet, Kandpal and Singh, 2013). These attacks come unexpected, and the victim is never prepared for taking action or guarding against such criminal behavior. It is often discovered much later, and often almost too late to terminate this kind of behavior.
This study seeks to analyze the current situation of cybercrime in Eswatini, based on published reports from regional and local organisations. Consequently, this paper will adopt the Routine Activity Theory based on the three required factors – likely offenders, suitable targets and the absence of capable guardians – to unpack the significance of cybercrime in Eswatini. Primarily, two questions will be asked: Which types of cybercrime are prevalent in the banking sector in Eswatini? What are the current measures proposed to restrain cybercrime in the banking sector? Therefore, this paper seeks to contribute to the ongoing debate regarding the applicability of the Routine Activity Theory to explain cybercrime.
2. Problem statement
Cybercrime over the years has become a major problem for a majority of banking institutions. The reliance on the Internet is one of the factors that has contributed towards cybercrime. Cyberattacks have become the most convenient method for cybercriminals to access confidential data located in the bank’s core systems through the Internet (Manivannan & Moorthy, 2020). Banking institutions are the most targeted institutions when compared to other industries because of the value of data kept within their structures. The contributing factor is the persistence of cybercriminals in learning new methods to penetrate banking systems. The global nature of the Internet has further allowed cybercriminals to commit almost any illegal activity anywhere in the world using cyberspace. The issue of cybercrime has become a contemporary issue for most banking institutions such that cybercriminals use every available opportunity and technique to gain access to banking systems. This has posed a great threat to the overall financial sector bearing in mind the huge losses in monetary value but more particularly in customer trust and confidence. It is therefore important that banking institutions ensure that proper safeguarding mechanisms should be put in place. Criminals in banking are often skilful and can therefore utilize a broad range of Information and Communications Technology (ICT) applications to penetrate, manipulate and attack bank accounts, information systems or more, and operate internationally, which makes cybercrime an extremely alarming threat to every country (Smith, 2015). Given that the cyberspace is borderless, criminals continually increase their capacities and activities to attack countries across the world, including Eswatini.
The study necessitated answers to the following questions: What were the most common mechanisms cybercriminals used to perpetuate cybercrime? Another question dealt with the availability of guidelines that provide guidance towards addressing cybercrime. Management’s perception of handling cybercrime was also investigated.
3. Cybercrime types in the banking sector
Wall (2001) categories cybercriminals into four groups: Cyber-trespass (infringing upon someone’s property and/or causing damages such as intrusion, humiliating and creating a virus), Cyber-deception and thefts (stealing money, property, or infringing intellectual property), Cyber-pornography (violating the rules of obscenity and human dignity), and Cyber-violence (causing psychological or other damage to a person), thereby violating human body protection. This way of classification divides the criminals into three groups of cybercrime criminals: “criminals against property”, “criminals against morality”, and “criminals against the person”. Aggarwal (2015) classified cybercrime into 13 types: Hacking (accessing a person’s computer without his knowledge to gain personal, confidential information), theft (violating and breaking copyrights to download data, which is known as pirated data), identity theft (stealing information about a bank account, credit card, debit card numbers and other confidential data to make a transaction under the victim’s name), defamation (hacking email accounts and sending negative emails to destroy the dignity of the victim), malicious software (using software to gain access to a system then steal confidential information and/or damage the hardware or software of the system), cyber stalking (bombarding the victim with online messages), e-mail harassment (harassing the victim by sending him letters, attachments), spoofing (acting as the victim to illegally have access to his data), fraud (stealing the victim’s money in his bank account by making transactions from his account), virus (loading onto a computer a program that causes damage to the system), Trojan horse (convincing the victim to download a code that harms the system), phishing (sending false emails to gain confidential information then use it against the victim), and grooming (creating a relationship with children for sexual exploitation).
4. Cybercrime trend in the Eswatini banking sector
The Kingdom of Eswatini is a developing country that has seen a steady increase in economic growth, due to advancement in technology and adoption of innovation strategies. With a population of about 1,15 million people, a mobile penetration rate of over 98%, with nearly 849 121 mobile broadband users and about 24 572 fixed broadband users, the scale of ICT adoption and the resulting impacts are increasingly noticeable across the Kingdom of Eswatini. This is a key motivation for the Kingdom of Eswatini to continue to leverage its legal and regulatory framework to promote the growth of ICTs and digitisation of its society and economy in a secure environment.
The Eswatini banking sector is a highly regulated environment and it complies with numerous pieces of legislation and regulations. To address such crimes, the Kingdom of Eswatini has instituted some legislative measures which include the Financial Institutions Act No. 6 of 2005, The Money Laundering and Financing of Terrorism (Prevention) Act of 2011, Prevention of Organized Crime Bill and Draft Computer Crime and Cybercrime Bill of 2013 and the Electronic Communications and Transactions Bill of 2017 (Government of Eswatini, 2019:1). There are five (5) banks in Eswatini, of which two (2) are local banks and the rest are established on a franchise platform. The banks also form part of an association called Eswatini Banking Association (EBA) which supports the banks in their growth and sustainability by encouraging efforts to minimise fraud.
Banking institutions provide many services for its customers that range from paying bills, cash transfer, opening and closing of accounts. The rapid development of the Internet also gave rise to other banking services such as mobile banking, cellphone banking and Internet banking. Over the past 4 years, the Central Bank of Eswatini has put in place considerable cyber-security measures such as recruiting cyber security professionals to implement more stringent policies and procedural measures, implementing software to identify, detect and counter cyber-attacks, upgrading core systems that had weaknesses exploited in the 2013 fraud and continuously driving cyber security awareness as to CBE staff (CBE, 2019).
An increase and adoption of digitalization by organizations result in an increase in cybercrime, due to the reliance and adoption of digital systems and networks for their business operations (Staal, 2015:11). The concentration of financial wealth in banks is one driver of cybercrime enabling a fertile ground for crime, and great potential for targeting by cybercriminals (Herlseman & Warren, 2004:260). Less developed countries are often exploited by cybercriminals due to their weak security controls, and these exploitations are then used to target more developed countries to gain access to their systems (Lakshmanan, 2019:1). The banking sector’s embrace of the digital world has left it more vulnerable to cybercrime. Banks provide many services to customers in order to keep up with the digitization era. Financial institutions now operating across varies jurisdictions, are at risk as online banking, frequent international transactions, innovative payment methods such as PayPal, and existence of databases in banks provide easy targets and high profits (Oliveria & Stickings, 2016:17). It has become necessary to protect financial institutions from the antics of cybercriminals, due to the pivotal roles of banks in the growth and economic development of any nation (Dzomira, 2013:16), since banks remain the favourite target of skilled cybercriminals (Lewis, 2018:9). Leuprecht (2019) affirms that cyberattacks in the banking sector are three times higher compared to other industries. The impact of cybercrimes in banks often leads to the failure to complete business and financial contracts created to deliver goods and services as well as intellectual property rights abuse. Banks are the most targeted due to the cybercriminal’s intention to damage the reputation of such firms (Onchomba, 2018:3).
5. Routine Activity Theory
The Routine Activity Theory attempts to explain human behaviour when an interaction takes place between the subject and its world. The patterns of crime will be affected if changes in routine activities influence the convergence of space and time of motivated offenders, suitable targets and the absence of capable guardians (Cohen & Felson, 1979:589). This theory proposes that three situations facilitating the occurrence of crime must occur at the same time and in the same space. The assessment of the situation determines whether or not a crime takes place. Crime is a product of the intersection of time and space of the potential criminal, suitable targets and the absence of capable guardians (Kodellas, Fisher & Wilcox, 2015:322).
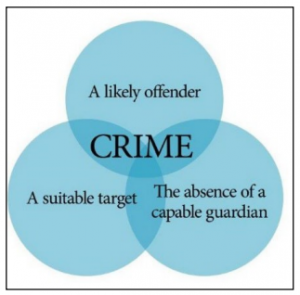
5.1 Suitable targets
A suitable target refers to an individual’s availability as a victim, including attributes of attractiveness to the offender (Cohen & Felson, 1979).
5.2 Capable guardians
Capable guardians include end-users, technical staff (network administrators) as well as automated protections such as firewalls, virtual private networks, anti-virus and anti-intrusion software, and ID authentication and access management systems (Leukfeldt & Yar, 2016).
5.3 Likely offenders
A likely offender refers to persons who are willing to commit a crime when an opportunity presents itself through the presence or absence of a capable guardian and target (Marcum, Higgins & Ricketts, 2010).
Aligning to this theory, the suitable targets are the bank customers accessing bank services either physically or online, the capable guardians referring to security measures such as authentication methods and the likely offenders referring to threat actors taking advantage of any opportunity to exploit. In the current situation where banking services are available online and online presence is ubiquitous, this theory is even more relevant.
6. Methodology
6.1 Sampling design and data collection
The study adopted the stratified random-sampling approach. Qualitative and quantitative methods were employed, using primary and secondary data. Primary data were collected from industry experts that work with cybercrime issues within the banking sector in Eswatini. The key participants in this study are the bank technical staff and specialist employees from departments in the banks and stakeholders that are mandated to address cybercrime issues and risks. These participants are the ones who are solely responsible and have a vested interest and knowledge of curbing cybercrime in the best interest of the banks. The secondary data were collected from various published reports available nationally and regionally and it included information obtained from the portals of the Central Bank of Eswatini, Ministry of ICT and cybersecurity working groups. Tables and graphs have been used to present comparative data analysis.
7. Findings
7.1 Cybercrime situation in Eswatini: reports
The Royal Eswatini Police Service has in recent years been reporting and detecting cybercrime activities, including identifying the perpetrators. However, like other law enforcement forces across the world, the Royal Eswatini Police Service continues to face difficulties in conducting investigations, collecting electronic evidence and prosecuting cybercrimes [ CITATION ICT21 \l 1033 ]. Eswatini banks have become victims of fraud between the years 2015 and 2017. In February 2015, Wesbank was defrauded of close to E3 million by a couple; in July 2015, a former Wesbank employee was arrested for E482 422; in July 2016 six (6) people were arrested for E20 million fraud at the Central Bank and in January 2017, E4.2M fraud was discovered at FNB (Khumalo, 2019:3).
|
Year |
Type of Crime |
Name of Bank |
Amount |
|
February 2015 |
Fraud |
Wesbank |
E3 million |
|
July 2015 |
Fraud |
Wesbank |
E482 422 |
|
July 2016 |
Fraud |
Central Bank |
E20 million |
|
January 2017 |
Fraud |
FNB |
E 4.2 million |
Table 1: Eswatini bank fraud cases (Khumalo, 2019:3)
Recently in the year 2020, the banking sector experienced a number of cybercrime cases according to the financial and economic crimes unit. The cybercrime statistics show that ATM Fraud, card cloning, investment fraud and Internet fraud were the most common in the year 2020.
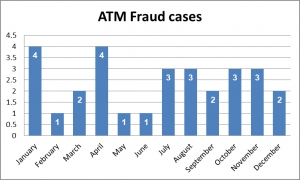
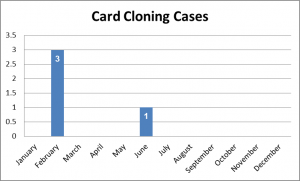
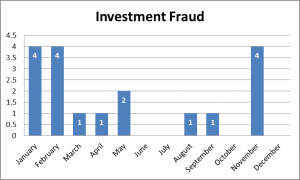
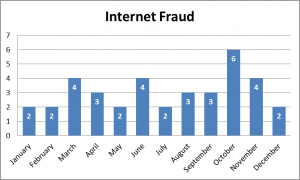
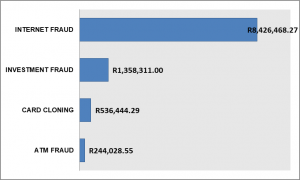
Internet fraud in this context consists of online trade, change of beneficiary details and account takeover incidents. Investment fraud consists of cryptocurrency, forex trading and Ponzi/pyramid schemes.
7.2 Cybercrime situation in Eswatini: industry experts
Views from the industry experts are also in line with the statistics given in Table 1 and also from Figure 1 to 4. Industry experts were asked about the most common mechanisms cybercriminals use to perpetuate cybercrime. Industry Expert 1 said, ”Social engineering is the most frequent type of attack we come across” while Industry Expert 2 affirms, “Cloning and skimming; SIM Card swapping and cloning; credential exploitation; social engineering; and phishing are the most recorded incidents we have experienced”.
7.3 Cybercrime guidelines
The industry experts were asked the about the availability of guidelines that provide guidance towards addressing cybercrime. Industry Expert A mentioned that: “Unfortunately we do not even have an IT structure that shows how the information technology processes and related departments should work together; however this is in the plan of action from our Headquarters”, while Industry Expert B had another view on this issue by stating: “At the moment we are guided by the IT Security Policy which I feel needs to be improved looking at how cybercrime is evolving, we also get regular training on how to handle cybercrime situations.” For Industry Expert C the response was more positive, “Yes, we do have policies and guidelines, and we implement it with efficiency.”
The existence of policies and guidelines is a good approach of how the banks can address cybercrime incidents. The industry experts were further asked about the existence of a cybersecurity strategy, and if it gets implemented or not. Industry Expert C stated: “Yes we do have a cybersecurity strategy and it defines programs and controls that align with the strategy and we also implement it incrementally,” while Industry Expert B affirmed by saying: “Yes, a cybersecurity strategy exists and the Board is aware of it.” Industry Expert A concluded: “Yes. We define programs and controls that align to the strategy and implement it incrementally.”
7.4 Management’s perception of handling cybercrime
The cybersecurity industry experts’ assessment regarding the level of handling cyber-attacks was fairly satisfactory. The industry experts were confident about their management’s perception of handling cybercrime issues. One industry expert said: ”Our management is comfortable with the whole cybercrime issue from prevention all the way to mitigation handling.” Industry Expert 2 supported by saying: “Cyber security is the number one topic in our organisation because it has become our core service to our customers.” Moreover, when asked about other factors that contribute to cybercrime within the organization, Industry Expert One said: “Disgruntled employees, lack of awareness, poor IT security infrastructure, bad configuration of our IT systems definitely contribute to cybercrime within the organization” and Industry Expert 2 confirmed: “Not applying the controls that are raised via the awareness activities causes the institution to suffer severe losses by cybercrime operations.”
Cases of fraudulent cash withdrawals, account information hacking, data theft and credit/debit card scams have remarkable association with electronic systems in banking business. Today, with the maximum information being online, banks and their clients are highly susceptible to being attacked by cyber criminals (Soni & Neena, 2013).
8. Discussion
8.1 Overview of cybercrime in Eswatini
Eswatini as a small country is not immune to cybercrime, and a specific theory such as the Routine Activity Theory shows that as long as the three elements (lack of a capable guardian, potential target and likely offender) coincide, the likelihood of crime to occur is high. From the findings it shows that the most common types of cybercrimes were Internet fraud, investment fraud, card cloning and ATM fraud.
8.2 High cybercrime potential
The high number of cybercrime cases is due to the lack of resources that can deal with the ever increasing cases. The development of the Eswatini Cybersecurity Strategy 2021 – 2025 will greatly assist the country in mitigating most of these attacks.
8.3 Cybercrime mitigation
The existence of a cybersecurity strategy shows that the banks have a tool that assists in addressing cybercrime activities. The response from the participants indicates that the strategy is aligned and shared with all the relevant stakeholders within the bank structure.
9. Conclusion
To further enhance cybercrime security within the banks, the following issues may be considered: The Routine Activity Theory envisages that changes in opportunity can increase the convergence of motivated offenders and suitable targets in the absence of capable guardianship (Govender, Watson & Amra, 2021).
References
Bamrara, A., Singh, G. & Bhatt, M. 2013. Cyber Attacks and Defense Strategies in India: An empirical assessment of banking sector. International Journal of Cyber Criminology, 7(1):49 – 61.
Central Bank of Eswatini. 2019. Towards a cyber resilient Central Bank. https://www.centralbank.org.sz/towards-a-cyber-resilient-central-bank/ Date of access: 18 Nov. 2021.
Chigada, J.M. 2020. ‘A qualitative analysis of the feasibility of deploying biometric authentication systems to augment security protocols of bank card transactions’. South African Journal of Information Management, 22(1):1194. https://doi.org/10.4102/ sajim.v22i1.1194 Date of access: 7 Nov. 2021.
Dzomira, S. 2013. Electronic fraud (Cyber fraud) risk in the banking industry, Zimbabwe. Risk governance & control: financial markets & institutions, 4(2):16-26.
http://www.academia.edu › Date of access: 29 Okt. 2021.
Cohen, L. & Felson, M. 1979. Social change and crime rates trends: A routine activity approach. American Sociological Review, 44, pp. 588-608.
Emm, D. 2020. Cyberattacks in Africa comparable to other parts of the globe. https://www.africanews.com/2021/07/20/cyberattacks-in-africa-comparable-to-other-parts-of-the-globe-says-kaspersky//. Date of access: 13 Sept. 2021.
Govender, I., Watson, B.W.W & Amra, J. 2021. Global virus lockdown and cybercrime rate trends: A Routine Activity Approach. Journal of Physics: Conference Series.
Kodellas, S., Fisher, B.S. & Wilcox, P. 2015. Situational and dispositional determinants of workplace victimization: The effects of routine activities, negative affectivity, and low self- control. International review of victimology, 21(3):321-342.
ICT, M.O. 2021. Eswatini National Cybersecurity Strategy – 2025.
Leukfeldt, E.R. & Yar. M. 2016. Applying Routine Activity Theory to Cybercrime: A Theoretical and Empirical Analysis Deviant Behavior 37(1):263–80.
Kshetri, N. 2019. Cybercrime and Cybersecurity in Africa. Journal of Global Information Technology Management. Date of access: 26 Nov. 2021.
Khumalo, S. 2019. Recent Bank Fraud Cases. Times of Swaziland, p.3
Marcum, C.D., Higgins, G.E. & Ricketts, M.L. 2010. Potential factors of online victimization of youth: An examination of adolescent online behaviors utilizing routine activity theory Deviant Behavior 31(1):381–410.
Manivannan, A. & Moorthy, D. 2020. Cyberattacks in the banking industry. ResearchGatehttps://www.researchgate.net › publication › 347441140 Date of access: 22 Nov. 2021.
Smith, G.S. 2015. “Management models for international cybercrime”. Journal of Financial Crime, 22 (1):04-125, 1(7) 22 – 27 July.
Thwala, N. 2019. Central Bank wary of cybercrime. Swazi Observer, p.15
Vineet Kandpal & Singh, R.K. 2013. Latest Face of Cybercrime and Its Prevention in India, International Journal of Basic and Applied Sciences, 2:150-156.
Wall, D.S. 2001. “Crime and the Internet: Cybercrimes and Cyber fears”. New York, Routledge.